Step-by-step guide for connecting Oracle site-to-site vpn to Opnsense as CPE.
Oracle OCI Side
1a) Go to “Networking > Customer connectivity > Site-to-Site VPN, or just search “VPN”.
1b) Choose “Customer-premises equipment” on the left, and create a new CPE.
(CPE means your own equipment, which is Opnsense in this case)
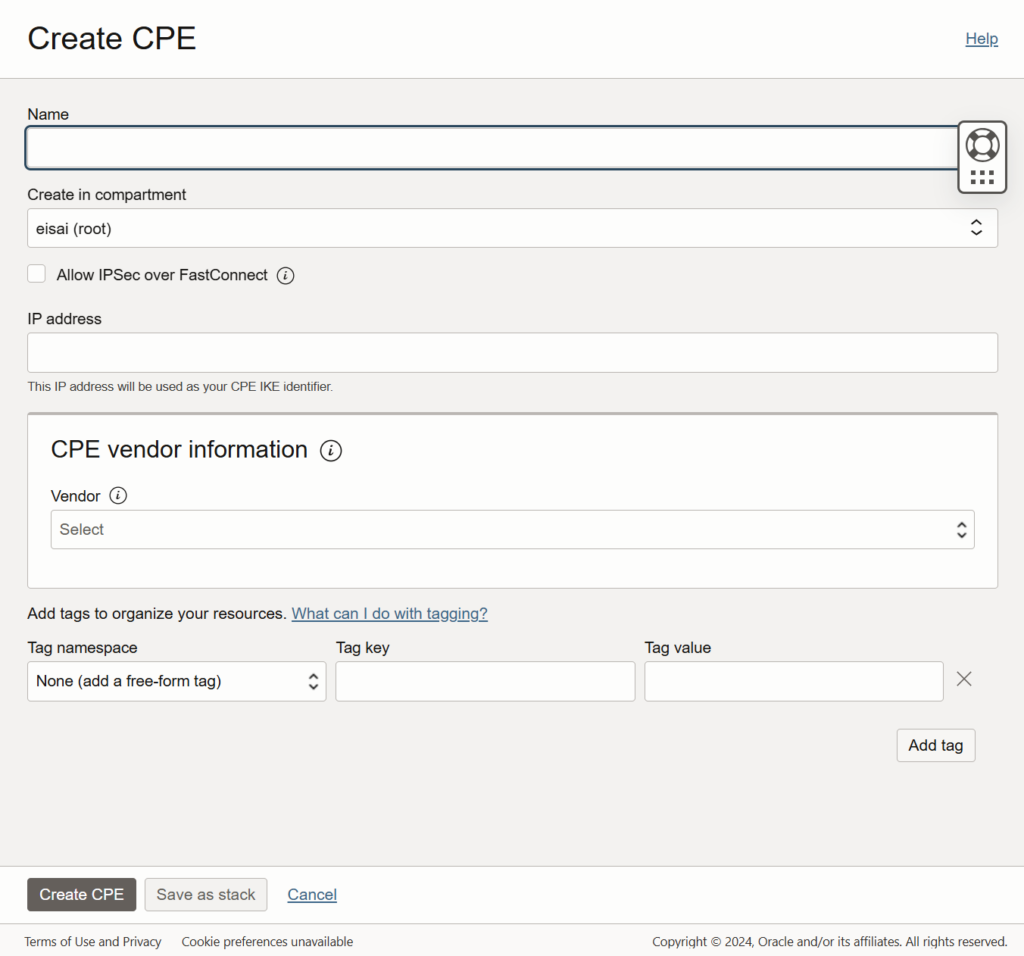
- Name: <any name>
- IP address: <your Opnsense WAN IP>
- CPE vendor information: Other
1c) Back to “Site-to-Site VPN” and Create IPSec connection
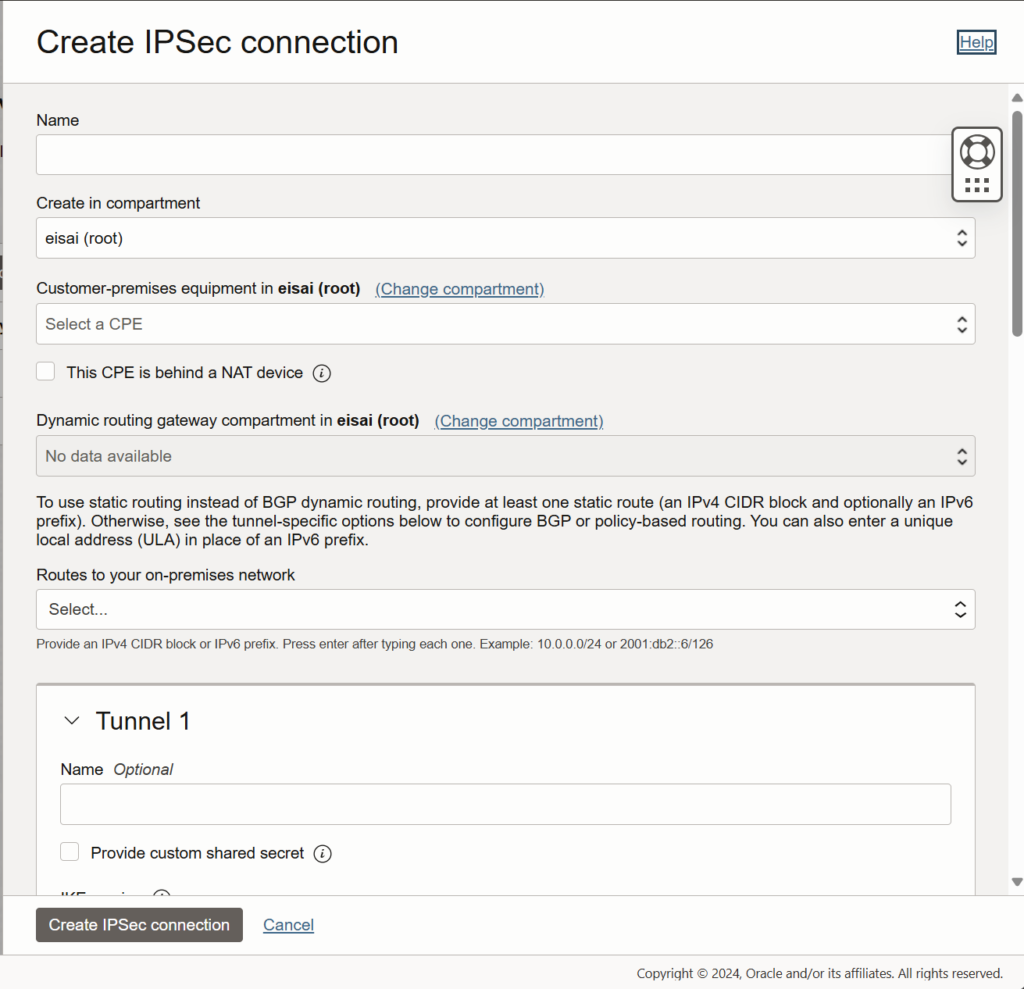
- Name: <any name>
- Customer-premises equipment: <The one you just created>
- This CPE is behind a NAT device: <Enable NAT-T or not>
Enable it if you don’t have a WAN IP on your Opnsense.
If you un-check it, it will still be set to “Auto”
When enabled, it will use port 500 and fallback to 4500, when disabled, it will only use 4500 - Routes to your on-premises network: <Subnets on your Opnsense end> e.g.: 192.168.1.0/24
1d) the Tunnel options needs extra attention. (But you can always change it later)
- Name: <any name>
- IKE version: IKEv2
- Routing type:
The most important option here, all 3 types can work, depending on your preference.
And what you choose will decide how we config Opnense next.
BGP dynamic routing:
(recommended)
Dynamic routing
Need VTI
plugin “os-frr” needs to be installed on Opnsense
IPsec security policy will not be installed to the kernel(or simply think the routing table from IPsec will not install). Once Phase 1 and 2 are established, we will create a P2P virtual tunnel interface(VTI), then pass routing entry on each side via BGP protocol.
Static routing:
(not recommended)
Need VTI
Same as BGP, we don’t install routing entry and we use VTI once Phase 2 is reached. But instead of using BGP to learn routing entries automatically, we create static route entries on both sides manually.
Policy based routing:
Sample
Still need to add static routes on Opnsense manually
IPsec handles everything, so we don’t need VTI. when connecting, route entry will be negotiated and installed on Phase 2.
(You can choose different types for each tunnel, but not recommended)
(From here, everything you configured needs to be matched on both sides)
1d-1) For BGP dynamic routing
- BGP ASN: <number from 64512 to 65535>
- IPv4 inside tunnel interface – CPE: <IP Address for the P2P connection> (Opnsense End)
this address will later be used for BGP peering. e.g.:10.100.1.3/31 - IPv4 inside tunnel interface – Oracle: <IP Address for the P2P connection> (Oracle End)
this address will later be used for BGP peering. e.g.:10.100.1.2/31 - IPv6 addressing: <Check if you have ipv6 subnet>
IPv6 inside tunnel interface(s): same usage as above, e.g.: fe50:cafe:100:1::3/127
1d-2) For Static routing:
Same as BGP, you just don’t need the “BGP ASN” and “IPv4 inside tunnel interface”
1d-3) For Policy based routing:
- On-premises CIDR blocks: <Subnets on Opnsense> (Usually same as the “Routes to your on premises network” on 1c)
- Oracle Cloud CIDR blocks: <Subnets on Oracle>
IPv4 inside tunnel interface(s): <not needed>
1e) Click “Show advanced options” and config encryption
Check “Set custom configurations”
Phase one (ISAKMP) configuration
- Custom encryption algorithm: AES_256_CBC
- Custom authentication algorithm: SHA_256
- Custom Diffie-Hellman group: GROUP14
Phase two (IPSec) configuration
- Custom encryption algorithm: AES_256_CBC
- Custom authentication algorithm: HMAC_SHA2_256_128
- Perfect forward secrecy Diffie-Hellman group: GROUP14
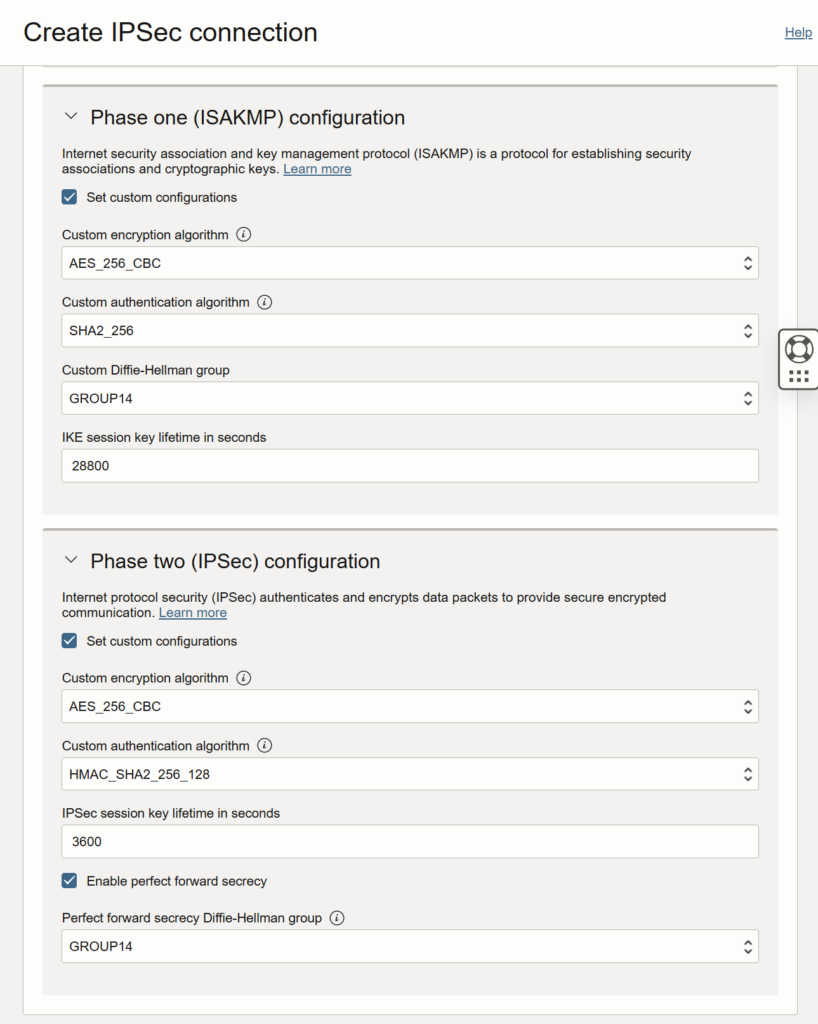
1f) Finally, Create IPSec connection
Opnsense Side
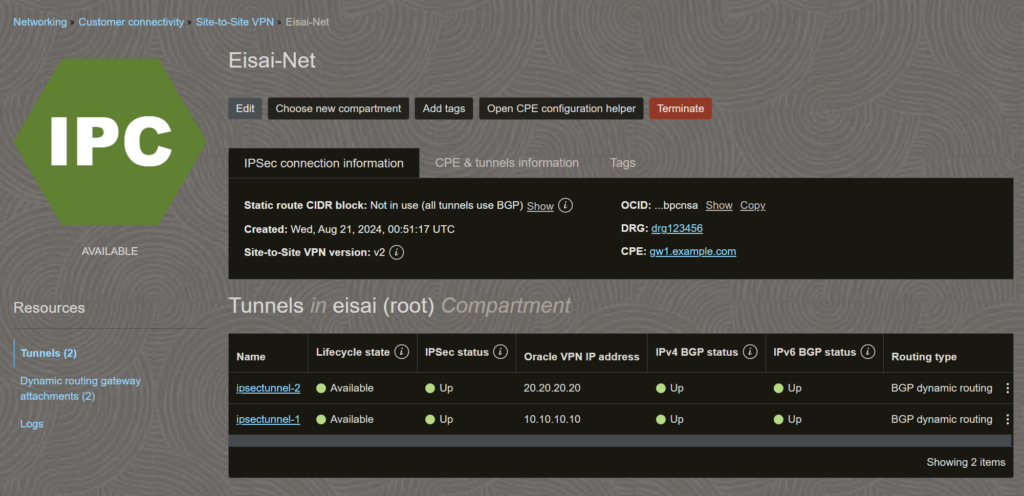
2a) On OCI, go to “Networking > Customer connectivity > Site-to-Site VPN > <the VPN you just created>
Switch to “CPE & tunnels information” tab, and put it on the side, you will find all the information you need next here.
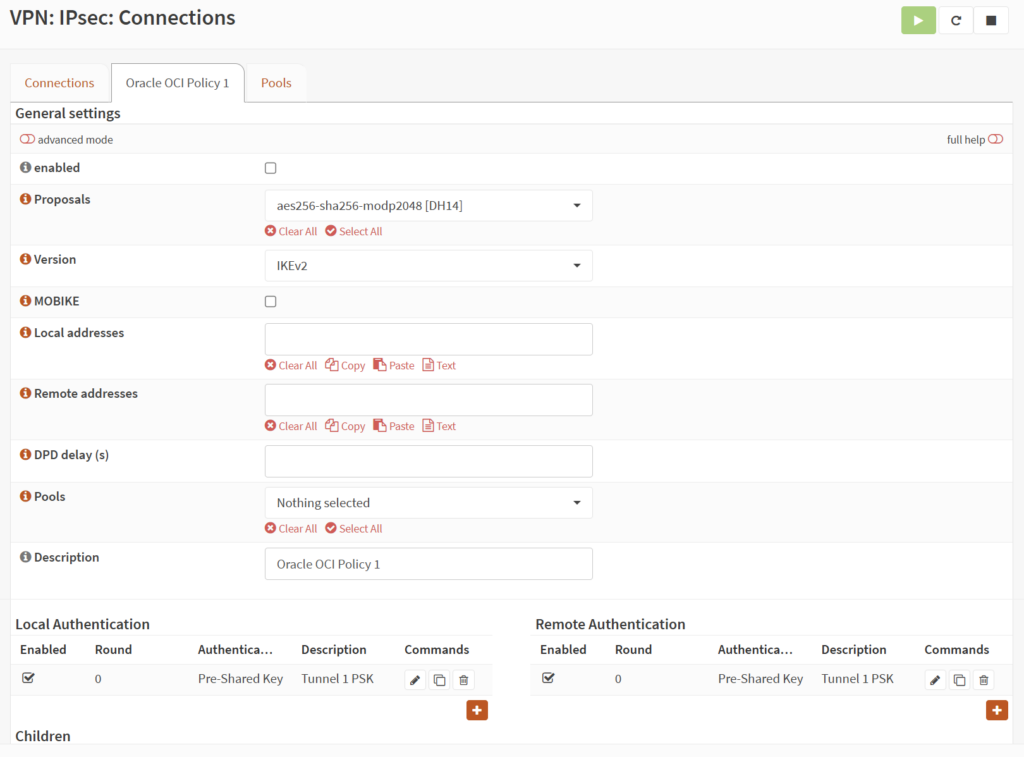
2b) On Opnsense, go to “VPN > IPsec > Connections”, click the “+”. (Don’t enable IPsec before everything is configured.)
Config for each tunnel at a time
- Proposals: aes256-sha256-modp2048 [DH14]
- Version: IKEv2
- MOBIKE: un-check
- Local addresses: <the address use to initiate VPN connection>
Usually Opnsense WAN IP. You can also use your domain name if you have DNS/DDNS. - Remote addresses: <see “Oracle VPN IP address” in step 1a>
- DPD delay (s): 20 (Or you can set your own on step 1e)
- Description: <give it a name>
- Save
2c) Under “Local Authentication”, click “+”
- Connection: <profile name>
- Authentication: Pre-Shared Key
- Id: <leave it blank>
leave it blank will default to the “Local address” you set on 2b. need to match the “CPE IKE identifier” on OCI (step 2a) - Certificates: <None>
- Description: <give it a name>
2d) Under “Remote Authentication”, click “+”
- Connection: <profile name>
- Authentication: Pre-Shared Key
- Id: <match the “Oracle VPN IP address” on OCI (step 2a)>
- Certificates: <None>
- Description: <give it a name>
2e) Under “Children”, click “+”
- Connection: <profile name>
- Mode: Tunnel (OCI only supported Tunnel mode)
- Start action: Trap+start
- DPD action: Clear
- ESP proposals: aes256-sha256-modp2048 [DH14]
2e-1) For “BGP dynamic routing” and “Static routing”
- Policies: UN-CHECK (IMPORTANT)
Failed to do so will result in loss of all connections once IPsec is initiated. - Local: 0.0.0.0/0
- Remote: 0.0.0.0/0
(If you have ipv6, use “0.0.0.0/0,::/0” for both) - Reqid: <any number>
Cannot be blank, and needs to be unique. e.g.: 10 for tunnel 1, 20 for tunnel 2. - Description: <give it a name>
2e-2) For “Policy based routing”
- Policies: checked
- Local: <match “On-premises CIDR blocks” you gave on 1d-3>
- Remote: <match “Oracle Cloud CIDR blocks” you gave on 1d-3>
- Reqid: <any number>
Cannot be blank, and needs to be unique. e.g.: 10 for tunnel 1, 20 for tunnel 2. - Description: <give it a name>
2f) Go to “VPN > IPsec > Pre-Shared Keys”, Click “+”
- Local Identifier: <ID you gave on step 2c> (Should be your WAN port IP by default)
- Remote Identifier: <ID you gave on step 2d>
- Pre-Shared Key: <You can found it on step 1a, “Shared secret”>
- Type: PSK
2g) “Policy based routing” Skip this step.
Go to “VPN > IPsec > Virtual Tunnel Interfaces”, Click “+”
- Reqid: <Reqid you given on step 2e-1>
- Local address: <You WAN port IP>
- Remote address: <see “Oracle VPN IP address” in step 1a>
- Tunnel local address: <see “IPv4 inside tunnel interface – CPE” on step 1d-1>
- Tunnel remote address: <see “IPv4 inside tunnel interface – Oracle” on step 1d-1>
- Name: <give it a name>
- (If you set up for ipv6 address on 1d-1, put ipv6 address into “Tunnel secondary address(es)” accordingly)
2h) Clone profiles for tunnel 2
- Clone, VPN > IPsec > Connections
Change “Remote addresses“
Change “ID” under “Remote Authentication” - Clone, VPN > IPsec > Pre-Shared Keys
Change “Remote Identifier“ - Clone, VPN > IPsec > Virtual Tunnel Interfaces (Skip for “Policy based routing”)
Change “Tunnel local address“
Change “Tunnel remote address“
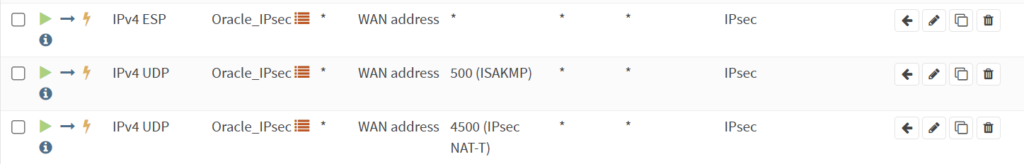
2i) Allow IPsec traffic
Go to “Firewall > Rules > WAN”, Allow the following ports
- Protocol: IPv4 ESP
Port: * - Protocol: IPv4 UDP
Port: 500 - Protocol: IPv4 UDP
Port: 4500
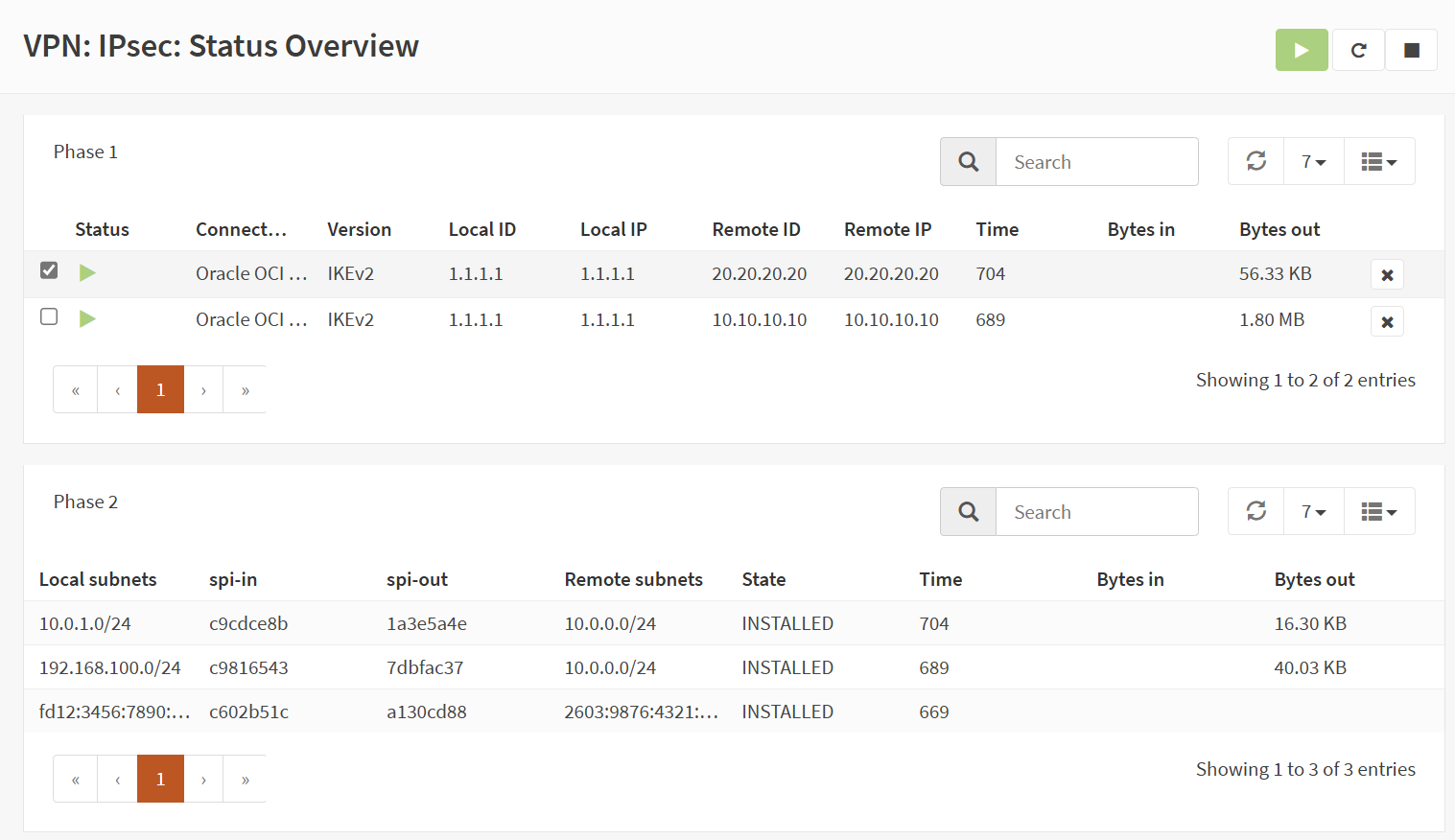
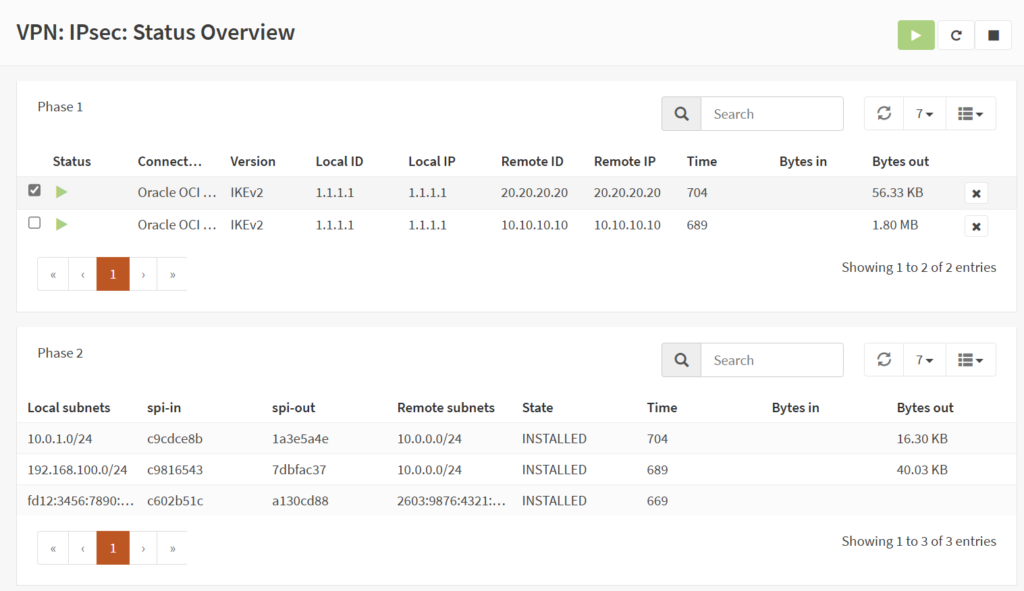
2j) Enable IPsec, go to “VPN > IPsec > Status Overview”
You should see connections successfully established.
Add Route
3a) Allow traffic on interface “IPsec”
(BGP dynamic routing & Static routing) Allow traffic on your VTI(s)
Adjust security list on OCI as well
3b) On OCI, Go to “Networking > Virtual cloud networks > Virtual Cloud Network Details > Subnets”
Choose your subnet, then the routing table of it.
Add all the Opnsense subnets to it, and point to the Dynamic Routing Gateway.
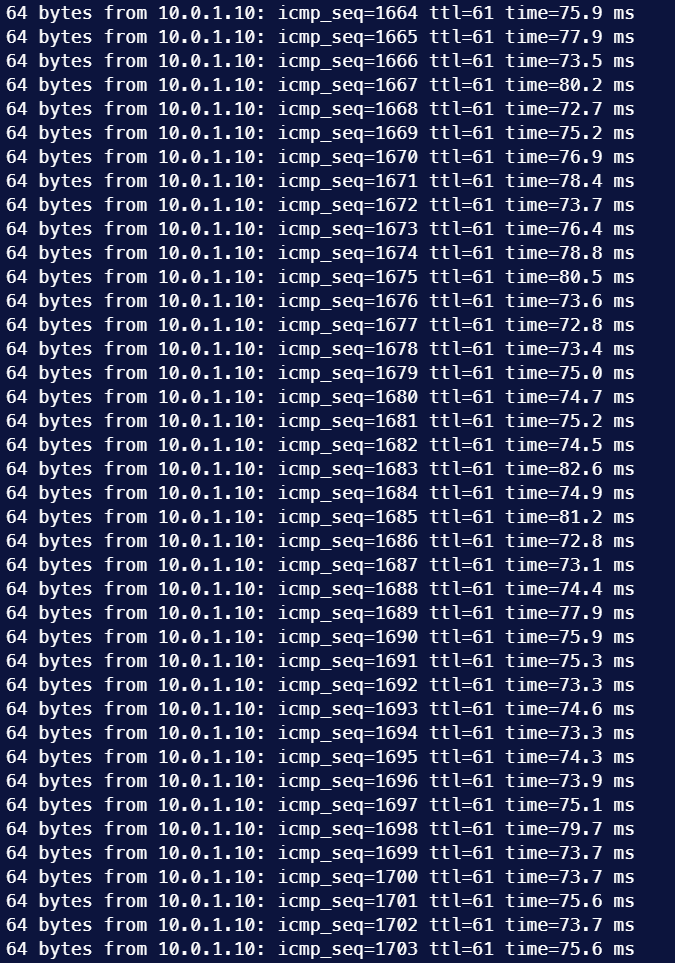
If you chose “Policy based routing“, then congratulations, you should able to send traffic to the VPN now. Your job is done.
3c-1) For “BGP dynamic routing”, on Opnsense, go to “Routing > BGP”
Under “General” Tab
- BGP AS Number: <match “BGP ASN” you gave on 1d-1>
- Network: <Opnsense subnets>
Under “Neighbors” Tab
- Peer-IP: <see “IPv4 inside tunnel interface – Oracle” on OCI (step 2a)>
- Remote AS: <see “Oracle BGP ASN” on OCI (step 2a)>
- Update-Source Interface: <VTI Interface>
Repeat the process for tunnel 2 and ipv6.
Enable “BGP” and “Routing” in “General”, congratulations, you should able to send traffic to the VPN now. Your job is done.
3c-2) For “Static routing”, on Opnsense, go to “System > Gateways > Configuration”
Add 2 of your VTI interface as Gateway
IP Address: <see “IPv4 inside tunnel interface – Oracle” on OCI (step 2a)>
Un-check “Disable Gateway Monitoring“, then add 2 gateways into a group, so you can have redundancy.
Go to “System > Routes > Configuration”, click “+”
- Network Address: <Your OCI subnets>
- Gateway: <Your VTI interface>
Repeat it for every subnet on Oracle.
Congratulations, you should able to send traffic to the VPN now. Your job is done.